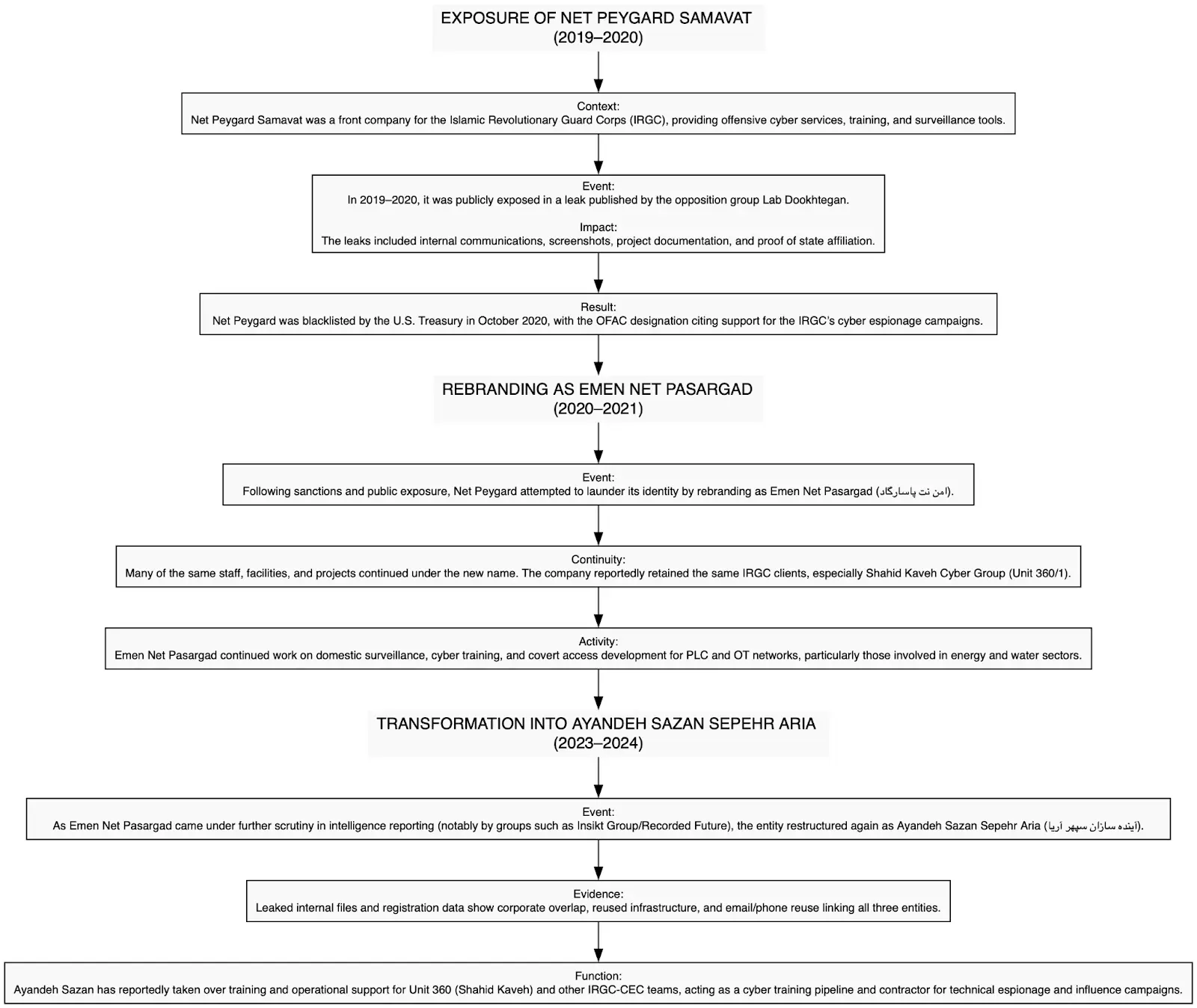
Iranian cyber operatives have intensified their assault on American critical infrastructure, with Intelligence Group 13 emerging as a primary threat actor targeting water treatment facilities, electrical grids, and industrial control systems across the United States.
The group, operating under the umbrella of the Islamic Revolutionary Guard Corps (IRGC) Shahid Kaveh Cyber Group, has demonstrated sophisticated capabilities in penetrating and compromising industrial control systems, particularly Unitronics programmable logic controllers (PLCs) that manage essential infrastructure operations.
The threat landscape has evolved significantly as Iranian hackers employ a multi-faceted approach combining technical sabotage with psychological warfare operations.
.webp)
Their recent campaigns have successfully infiltrated water treatment facilities in Pennsylvania, including the highly publicized Aliquippa water system attack, where attackers gained unauthorized access to control systems and leaked compromising screenshots through their propaganda channels.
These operations represent a concerning escalation in state-sponsored cyber warfare, targeting civilian infrastructure that millions of Americans depend on daily.
.webp)
Intelligence Group 13’s operational methodology centers on pre-positioning malware within target environments, creating dormant implants that can be activated for future sabotage operations.
DomainTools researchers identified the group’s sophisticated tradecraft, which includes deploying custom malware tools such as IOControl and Project Binder specifically designed to manipulate industrial control systems.
The attackers leverage phishing campaigns, credential theft, and open-source intelligence gathering to gain initial access to target networks, subsequently establishing persistent footholds within critical infrastructure environments.
The group’s technical arsenal demonstrates advanced understanding of industrial control systems architecture, with particular expertise in exploiting Unitronics PLCs commonly used in water treatment and distribution facilities.
.webp)
Their attack vectors typically involve credential harvesting through spear-phishing operations, followed by lateral movement within operational technology networks to reach supervisory control and data acquisition (SCADA) systems.
Persistence and Evasion Tactics
Intelligence Group 13 employs sophisticated persistence mechanisms that allow their malware to remain undetected within compromised systems for extended periods.
Their approach involves embedding malware implants deep within industrial control networks, often masquerading as legitimate system processes or maintenance utilities.
.webp)
The group’s IOControl malware demonstrates advanced evasion capabilities, utilizing legitimate system APIs and communication protocols to blend with normal network traffic.
The malware’s persistence strategy includes establishing multiple redundant access points within target networks, ensuring operational continuity even if primary implants are discovered and removed.
Technical analysis reveals that the attackers implement time-based activation triggers, allowing malware to remain dormant until specific conditions are met or predetermined dates arrive.
This approach enables the threat actors to maintain long-term access while minimizing detection risks during routine security monitoring.
Their CyberAveng3rs propaganda arm serves a dual purpose beyond psychological warfare, acting as a communication channel for operational coordination and threat intelligence dissemination.
The group’s ability to leak control panel screenshots and system configuration details demonstrates comprehensive access to target environments, highlighting the severity of their infrastructure penetration capabilities.
Investigate live malware behavior, trace every step of an attack, and make faster, smarter security decisions -> Try ANY.RUN now



